AI in Fraud Prevention: Transforming Security in the Digital Age
Key Insights

The Evolution of Fraud
The digital transformation has dramatically changed how fraudsters operate. Traditional legacy systems are becoming increasingly ineffective against sophisticated cyber threats, struggling with:
- High false positive rates
- Lack of adaptability to new fraud tactics
- Slow detection processes
AI’s Role in Fraud Prevention

Real-Time Detection Capabilities
Artificial Intelligence has revolutionized fraud prevention by:
- Analyzing massive datasets in seconds
- Identifying unusual patterns and behaviors
- Continuously learning and adapting to new fraud tactics
- Reducing false positives and improving detection accuracy
Industry Applications

- Financial Services
- Improved identity verification
- Detecting unauthorized transactions
- Analyzing driver’s licenses and passports
- Reducing identity fraud by up to 37% in 2023
- E-Commerce
- Detecting bot-generated fake reviews
- Analyzing purchasing behaviors
- Authenticating users through facial recognition

- Insurance
- Cross-referencing claims with medical records
- Detecting fabricated or exaggerated claim narratives
Technological Approaches
Facial Recognition
- Account verification
- Transaction security
- Anti-spoofing techniques
- Biometric authentication

Emerging Technologies
- Federated learning
- AI and blockchain integration
- Advanced machine learning algorithms

Challenges and Considerations
- Data Privacy and Security
- Protecting sensitive biometric data
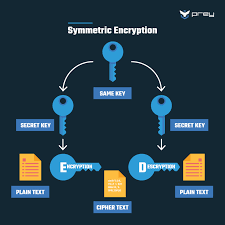
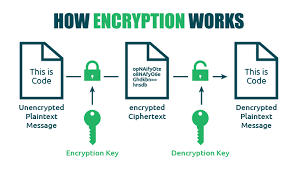
- Implementing strong encryption protocols
- Ensuring regulatory compliance

- Accuracy and Bias
- Addressing environmental factors
- Minimizing false positives and negatives
- Improving recognition accuracy
Future Outlook
AI in fraud prevention continues to evolve, promising:
- More advanced security solutions
- Real-time threat detection
- Enhanced user trust
- Collaborative learning across institutions

Conclusion
Organizations must embrace AI-driven fraud prevention technologies while remaining vigilant about privacy, bias, and regulatory concerns.
Fraud Detection in Singapore: AI-Powered Approaches
Singapore’s Unique Fraud Landscape
Technological Context
Singapore is a global financial hub with:
- Advanced digital infrastructure
- High technology adoption rates
- Sophisticated cybersecurity ecosystem

Key Fraud Detection Methods
1. Financial Sector Fraud Prevention
AI-Powered Techniques
- Real-time transaction monitoring
- Behavioral pattern analysis
- Machine learning anomaly detection
Singapore-Specific Considerations
- Compliance with Monetary Authority of Singapore (MAS) regulations
- High emphasis on financial technology (FinTech) innovation
- Stringent Know Your Customer (KYC) requirements

2. Facial Recognition Technologies
Implementation Strategies
- Government-backed biometric authentication
- Multimodal verification systems
- Advanced anti-spoofing algorithms

Local Applications
- SingPass digital identity verification
- Banking sector identity authentication
- Government service access control
3. E-Commerce Fraud Prevention
Detection Mechanisms
- Behavioral pattern tracking
- Machine learning-powered review analysis
- Transaction risk scoring
Singapore’s Digital Economy Focus
- Protection of digital marketplace platforms
- Safeguarding against cross-border fraudulent activities
- Supporting local and international e-commerce ecosystem
Advanced Technological Integration
AI and Blockchain Synergy
- Transparent transaction records
- Decentralized fraud detection
- Enhanced security protocols
Federated Learning Approach
- Collaborative fraud intelligence sharing
- Maintaining individual data privacy
- Cross-institutional learning networks
Regulatory and Ethical Considerations
Data Protection Frameworks
- Personal Data Protection Act (PDPA) compliance
- Strict data encryption standards
- Transparent user consent mechanisms
Bias Mitigation in AI Systems
- Diverse training data sets
- Regular algorithmic audits
- Inclusive technology development
Emerging Fraud Risks in Singapore
- Cryptocurrency fraud
- Social engineering attacks
- Digital identity theft
- Cross-border cybercrime
Recommendations for Organizations
- Invest in AI-powered fraud detection
- Continuously update detection algorithms
- Maintain robust data protection measures
- Collaborate with regulatory bodies
- Develop adaptive security frameworks
Future Outlook
- Increased AI integration
- More sophisticated detection methods
- Proactive rather than reactive approaches
- Continuous technological evolution
Conclusion
Singapore’s approach to fraud detection represents a global benchmark, combining cutting-edge AI technologies with robust regulatory frameworks and a commitment to innovation and security.


.
Identity Theft
Identity theft is a pervasive form of fraud that can have devastating consequences for victims. In this crime, the perpetrator steals an individual’s personal information to assume their identity. This stolen information can often be gathered from discarded documents such as bank statements, utility bills, or even phishing scams.
Once armed with this data, the criminal may choose to open accounts in the victim’s name, a process known as application fraud. They might apply for credit cards, loans, or utility services under pretences, leaving the unsuspecting victim to deal with the aftermath.
The emotional toll of identity theft can be immense. Victims often face financial losses and damage to their credit scores, which can take years. In today’s digital age, account takeovers have become a prevalent threat to unsuspecting victims. Criminals typically employ tactics such as phishing, vishing, or smishing to manipulate individuals into revealing their personal information.

Phishing often involves deceptive emails that appear to come from legitimate sources. These emails may prompt the victim to click on malicious links or provide sensitive details under the guise of verifying their identity.
Vishing, or voice phishing, involves phone calls in which scammers impersonate bank representatives or trusted entities to extract confidential information directly from the victim. Similarly, smishing involves text messages that lure individuals into divulging critical data.
Once armed with this personal information, the criminal can easily convince a bank to change the account holder’s address. This deception allows them full access to the victim’s financial accounts and resources.

Additionally, some criminals are skilled enough to bypass bank interaction altogether. They can use the obtained credentials to log into online accounts directly, executing unauthorised transactions without needing any further verification.
The consequences for victims can be devastating, leading not only to financial loss but also emotional distress as they recover their stolen identities and secure their accounts. Consequently, individuals must remain vigilant and understand these risks to protect themselves against potential account takeovers for repair. Additionally, they may find themselves tangled in legal disputes as they try to prove their innocence.

Recovering from such a violation requires diligence and time, making it crucial for individuals to safeguard their personal information vigilantly. Implementing measures like shredding sensitive documents and monitoring credit reports can help prevent these types of crimes before they occur.
Maxthon
Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
 This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
The post AI in Fraud Prevention appeared first on Maxthon | Privacy Private Browser.