In a resounding victory against the ever-evolving landscape of financial fraud, a proactive partnership between the Singapore Police Force’s Anti-Scam Centre (ASC) and six major banks has successfully prevented over 8,700 bank customers from losing an estimated $73 million to sophisticated fraudulent schemes. This significant achievement was realized through a focused two-month joint operation, spanning from November 1, 2024, to December 31, 2024, which strategically leveraged technological advancements to identify and alert potential scam victims before they suffered irreversible financial damage.
The success of this operation underscores the critical role of collaboration and innovation in combating the pervasive threat of scams, which continue to plague individuals and communities worldwide. The rising sophistication of these scams necessitates a multi-faceted approach, combining law enforcement expertise with the technological capabilities and resources of financial institutions. This partnership serves as a model for other nations grappling with similar challenges, highlighting the efficacy of a proactive, data-driven strategy in protecting citizens from financial exploitation.
During the operation, the ASC and participating banks – DBS, UOB, OCBC, Standard Chartered, HSBC, and GXS – deployed cutting-edge robotic process automation (RPA) technology to meticulously analyze transaction data and identify individuals exhibiting behavioral patterns consistent with those targeted by prevalent scam types. These included, but were not limited to, deceptive job scams promising lucrative returns, sophisticated investment scams designed to lure unsuspecting investors, emotionally manipulative fake-friend call scams exploiting personal relationships, and fraudulent e-commerce scams capitalizing on online shopping trends.
Once individuals were flagged as potential scam victims, a targeted communication strategy was implemented. Over 13,000 SMS messages were dispatched to these identified individuals, delivering clear and concise warnings about suspicious account transfers and unequivocally advising against engaging in further transactions. These messages served as a critical intervention point, disrupting the scam’s momentum and providing individuals with the necessary information to reassess their situation and potentially avoid falling victim to the fraudulent scheme.
“Upon receiving the SMS alerts, a significant number of victims realized they had fallen prey to a scam and promptly filed police reports,” stated a police spokesperson. “This rapid detection and intervention resulted in the disruption of over 1,444 ongoing scams and the prevention of substantial financial losses. The swift action taken by these individuals, empowered by the timely alerts, played a vital role in minimizing the damage caused by these scams and bringing the perpetrators closer to justice.”
This operation marks the sixth collaborative effort between the police and banks in 2024 specifically aimed at combating the ever-evolving landscape of scams. Previous partnerships throughout the year have already proven highly effective, demonstrating the power of integrated strategies in tackling financial fraud. These joint initiatives have successfully identified and alerted potential scam victims in over 13,000 ongoing scams involving more than 55,600 potential victims and collectively protected over $420 million in savings that would have otherwise been lost to malicious actors.
The consistent success of these collaborative operations highlights the importance of sustained vigilance and continuous adaptation in the fight against scams. As scammers become increasingly sophisticated in their techniques, law enforcement and financial institutions must remain one step ahead, constantly refining their strategies and leveraging the latest technological advancements to identify and disrupt fraudulent activities. This requires a commitment to ongoing research, data analysis, and knowledge sharing, ensuring that the public remains protected from emerging scam tactics.
The public is strongly urged to remain vigilant, informed, and proactive in protecting themselves from becoming victims of scams. The key to preventing financial loss lies in recognizing the telltale signs of fraudulent schemes and taking immediate action to safeguard personal information and financial assets. For more comprehensive information and valuable resources on identifying and avoiding various types of scams, individuals are encouraged to call the Anti-Scam Helpline at 1799 or visit the dedicated scam awareness website at www.scamalert.sg. These resources offer crucial insights into prevalent scam tactics, empowering individuals to identify red flags and make informed decisions.
In conclusion, the successful collaboration between the Singapore Police Force’s Anti-Scam Centre and major banks represents a significant step forward in the ongoing battle against financial fraud. By embracing technological innovation and fostering a strong partnership between law enforcement and financial institutions, Singapore is setting a precedent for proactive scam prevention and protection of its citizens. The continued vigilance and proactive engagement of the public, armed with the knowledge and resources to identify and avoid scams, will be crucial in maintaining this momentum and further strengthening the nation’s defenses against the ever-present threat of financial exploitation. This collaborative approach serves as a potent reminder that by working together, we can create a safer and more secure financial environment for all.
General Protection Advice:
- Verify the identity of contacts through official channels
- Never share sensitive personal information online
- Be skeptical of urgent requests involving money
- Document evidence of scams for reporting
- Report incidents to the police and relevant organizations
- Contact banks immediately if financial information is compromised

Preventing Online Scams in Singapore
Based on the information provided, here are effective strategies to protect yourself from online scams in Singapore:
General Prevention Strategies
- Stay informed about current scam tactics – scammers constantly evolve their methods.
- Be skeptical of unsolicited communications (calls, emails, texts)
- Never share personal information unless you’ve verified the recipient’s legitimacy
- Verify independently – contact organizations through their official numbers/websites
- Review financial statements regularly to catch unauthorized charges early
- Take your time – legitimate organizations won’t pressure you to make immediate decisions
Specific Prevention Measures

For Cold Call Scams
- End suspicious calls immediately – simply say “No thank you” and hang up
- Don’t engage with or challenge suspected scammers
- Verify claims by contacting organizations through official channels
For Phishing Emails
- Check sender email addresses carefully (government emails end with .gov.sg)
- Look for spelling/grammar errors or poor graphics
- Don’t click links in suspicious emails – access websites directly
- Use email service provider tools to report phishing attempts
For Romance Scams
- Be wary of online relationships that progress unusually quickly
- Never send money to someone you haven’t met in person
- Limit sharing of personal details and photos
- Research the person’s profile and images online
For Subscription Scams
- Research companies before signing up for free trials
- Read terms and conditions carefully
- Set calendar reminders to cancel free trials
- Consider using direct debit instead of recurring card charges
- Review monthly bank statements for unexpected charges
For Sextortion
- Be cautious with friend requests from strangers
- Remember that video chats can be recorded even on encrypted apps
- Keep personal information private on social media
- Never engage in compromising activities with people you’ve just met online
When Victimized
- Report to police immediately
- For financial scams, contact your bank right away
- Document evidence (screenshots, messages, etc.)
- Use Singapore’s dedicated reporting channels:
- Police
- National Crime Prevention Council’s “X Ah Long” hotline (1800-924-5664)
- i-Witness service

These prevention strategies should help protect you from the most common scams targeting Singaporeans, though staying alert and maintaining healthy skepticism are your best ongoing defenses.
AI in Cybersecurity: Fighting Scams

Scale of the Problem:
- Scam victims in Singapore lost around S$650 million in 2023
- Singapore reported a record 46,563 scam cases in 2023
- Globally, cybercrime costs are projected to increase by USD 6.4 trillion from 2024-2029

GovTech’s Anti-Scam Products (GASP) Team:
- Mission: To build tech products that detect, deter, and disrupt scammers at scale
- Key personnel mentioned: Mark Chen (Principal Product Manager) and Andre Ng (Assistant Director)

SATIS (Scam Analytics and Tactical Intervention System):
- Developed by GASP in collaboration with the Ministry of Home Affairs
- Consolidates threat intelligence to analyze and disrupt malicious websites
- Powered by recursive Machine-Learning Site Evaluator (rMSE), an in-house ML technology
- Analyzes hundreds of thousands of URLs daily to identify potentially malicious sites
- As of September 2024, it has identified and disrupted over 50,000 scam-related websites

AI Implementation:
- Evolved from manual operators using static rules to ML systems identifying unknown patterns
- AI can analyze vast amounts of data quickly to detect anomalous behavior
- The system improves continuously as more data is fed into it

Data Poisoning Challenges:
- Data poisoning is when attackers corrupt training datasets to undermine AI/ML models
- GASP validates datasets carefully using verified police case data and the ScamShield database
- The team balances having large training datasets with ensuring data quality
- They implement patience in analysis, waiting weeks or months before determining if a site is safe, to counter “strategic squatting
Other Examples:
- The article mentions AI cybersecurity systems deployed at the Paris Olympic Games 2024, which monitored social media accounts in real time to protect athletes from online abuse
AI Cybersecurity Solutions to Tackle Scams
Based on the article, here’s an analysis of AI-based cybersecurity solutions for combating scams:
Current AI Solutions in Scam Prevention

1. SATIS (Scam Analytics and Tactical Intervention System)
- Core Technology: Recursive Machine-Learning Site Evaluator (rMSE)
- Capabilities:
- Analyzes hundreds of thousands of URLs daily
- Identifies potentially malicious websites
- Has disrupted over 50,000 scam websites as of September 2024
- Impact: Enables proactive hunting and takedown of malicious websites before victims are affected
- Key Advantage: Scale and speed not possible with human analysis alone
2. AI Monitoring at the Paris Olympics 2024
- Capabilities:
- Real-time monitoring of thousands of social media accounts
- Language processing across 35+ languages
- Flagging of abusive messages for quick intervention
- Coverage: Protected nearly 15,000 athletes and 2,000 officials
- Benefit: Allowed athletes to focus on competition without negative social media impacts

Technical Approaches in AI-Based Scam Detection
- Evolution from Static Rules to Machine Learning:
- Moving beyond fixed rule-based detection to pattern recognition
- Identifying unknown and anomalous behaviors automatically
- High-Volume Data Processing:
- Analyzing vast datasets rapidly
- Drawing logical conclusions on what constitutes anomalous behavior
- Continuous Learning:
- Systems improve over time as more data is processed
- Adaptation to new trends in attacker behaviors
- Code Analysis:
- Scanning millions of lines of code to identify vulnerabilities
- Suggesting safe code fixes to counter attackers
Challenges and Countermeasures
Data Poisoning
- Challenge: Malicious actors introducing corrupted data into training sets
- Solutions:
- Data Validation: Using verified sources like police reports
- Multiple Data Sources: Combining datasets like ScamShield reports
- Patience-Based Validation: Waiting periods before classifying websites as safe
- Balancing Quality vs. Quantity: Finding the optimal mix of data volume and quality
Strategic Squatting
- Challenge: Attackers registering domains with initially benign content before making them malicious
- Countermeasure: Implementing patience in analysis, monitoring sites over extended periods

Effectiveness Factors
- Quality of Training Data: Critically important for accurate detection
- Volume of Data: More data generally leads to better detection capabilities
- Validation Methods: Processes to ensure data integrity
- Adaptive Learning: Systems that evolve as scam tactics change
This analysis suggests that effective AI cybersecurity solutions require a combination of advanced machine learning, carefully curated datasets, and strategic approaches to validation that account for attackers’ evolving tactics.
General Scam Prevention Tips
- Trust your instincts
- If an offer seems too good to be true, it probably is
- Keep personal and financial information confidential
- Stay informed about the latest scam techniques
- Report suspicious activities to authorities
- Educate family members, especially older relatives
- Use secure, updated technology
- Maintain a healthy level of skepticism online

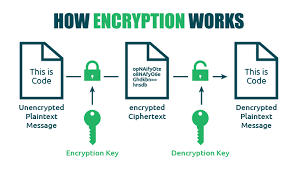
How Encryption Works

Encryption uses mathematical algorithms to convert plaintext (readable data) into ciphertext (scrambled data). Only those with the decryption key can convert the ciphertext back into usable information. There are two main types:
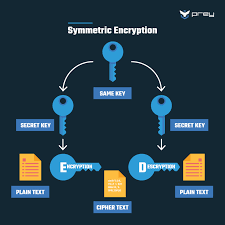
- Symmetric Encryption: Uses the same key for both encryption and decryption. It’s efficient but requires a secure key exchange.
- Asymmetric Encryption uses a pair of keys—a public key for encryption and a private key for decryption—to allow secure communication without prior key exchange.
Key Encryption Applications for Privacy
Device Encryption
- Full-disk encryption: Protects all data on your computer or smartphone (BitLocker for Windows, FileVault for Mac, and built-in encryption for iOS and Android)
- File-level encryption: Protects individual files and folders

Communication Encryption
- HTTPS: Secures website connections (look for the padlock icon in your browser)
- End-to-end encryption: Used in messaging apps like Signal, WhatsApp, and others to ensure only you and your recipient can read messages
- Email encryption: Options include PGP (Pretty Good Privacy), S/MIME, or encrypted email services
Network Encryption
- VPNs: Create an encrypted tunnel for all your internet traffic
- Wi-Fi encryption: WPA3 is the current most substantial standard for wireless networks
Cloud Storage Encryption
- At-rest encryption: Protects stored data
- Zero-knowledge encryption: The provider has no access to your encryption keys
- Client-side encryption: Data is encrypted before leaving your device

Implementing Encryption in Your Digital Life
- Enable device encryption on all your computers and mobile devices
- Use encrypted messaging apps for sensitive communications
- Verify HTTPS connections when sharing personal or financial information
- Consider encrypted email for sensitive communications
- Choose cloud services with strong encryption policies
- Use a VPN when connecting to public Wi-Fi networks
- Password-protect and encrypt sensitive files and backups
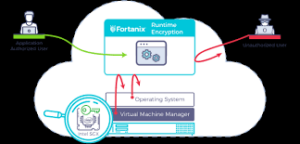
Limitations to Consider
- Encryption can’t protect against malware already on your device
- Weak passwords can undermine even the strongest encryption
- Encryption doesn’t hide metadata (who you’re communicating with, when, how often)
- Some countries have laws limiting encryption use or requiring backdoors

Encryption is a fundamental aspect of digital privacy that works best as part of a comprehensive security strategy. By understanding and implementing appropriate encryption methods, you can significantly enhance your online privacy protection.
.
Identity Theft
Identity theft is a pervasive form of fraud that can have devastating consequences for victims. In this crime, the perpetrator steals an individual’s personal information to assume their identity. This stolen information can often be gathered from discarded documents such as bank statements, utility bills, or even phishing scams.
Once armed with this data, the criminal may choose to open accounts in the victim’s name, a process known as application fraud. They might apply for credit cards, loans, or utility services under pretences, leaving the unsuspecting victim to deal with the aftermath.
The emotional toll of identity theft can be immense. Victims often face financial losses and damage to their credit scores, which can take years. In today’s digital age, account takeovers have become a prevalent threat to unsuspecting victims. Criminals typically employ tactics such as phishing, vishing, or smishing to manipulate individuals into revealing their personal information.

Phishing often involves deceptive emails that appear to come from legitimate sources. These emails may prompt the victim to click on malicious links or provide sensitive details under the guise of verifying their identity.
Vishing, or voice phishing, involves phone calls in which scammers impersonate bank representatives or trusted entities to extract confidential information directly from the victim. Similarly, smishing involves text messages that lure individuals into divulging critical data.
Once armed with this personal information, the criminal can easily convince a bank to change the account holder’s address. This deception allows them full access to the victim’s financial accounts and resources.

Additionally, some criminals are skilled enough to bypass bank interaction altogether. They can use the obtained credentials to log into online accounts directly, executing unauthorised transactions without needing any further verification.
The consequences for victims can be devastating, leading not only to financial loss but also to emotional distress as they recover their stolen identities and secure their accounts. Consequently, individuals must remain vigilant and understand these risks to protect themselves against potential account takeovers for repair. Additionally, they may find themselves tangled in legal disputes as they try to prove their innocence.

Recovering from such a violation requires diligence and time, making it crucial for individuals to safeguard their personal information vigilantly. Implementing measures like shredding sensitive documents and monitoring credit reports can help prevent these types of crimes before they occur.t to emerging challenges, Incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
Analysis of Scam Types and Prevention in Singapore
Based on the document, here’s an analysis of the scam types prevalent in Singapore and the prevention strategies being implemented:
Main Scam Types
- Self-Effecting Transfer Scams
- Most common type where victims willingly transfer money to scammers
- Psychological tactics target emotions like desire for companionship, respect for authority, and greed
- Victims often refuse to believe they’re being scammed

- Malware and Phishing Attacks
- Target bank accounts and online credentials
- Often involve sophisticated technical deception
- Phone/SIM-Based Scams
- Scammers using local phone numbers to make calls and send SMS
- Creates a false sense of legitimacy
- Cryptocurrency Scams
- Fake crypto trading interfaces that simulate profits
- Malware/phishing to drain crypto wallets
- Requesting victims convert money to cryptocurrency to evade banking safeguards
- Social Media and Messaging App Scams
- 60% of scams occur through these platforms
- Telegram specifically mentioned as a platform of concern (scam reports doubled in 2024)

Prevention Strategies
Government Regulatory Measures

- Protection from Scam Bills (January 2025)
- Empowering police to temporarily restrict banking transactions as a last resort
- Target cases where victims refuse to believe they’re being scammed
- SIM Card Regulations
- Limits on post-paid SIM card ownership
- Criminalization of SIM card misuse and transfer
- Penalties for SIM card abuse in scams
- Online Criminal Harms Act
- Requires online services to implement anti-scam measures
- Encourages robust user verification against government-issued IDs
- Potential for additional legislative action against platforms like Telegram
Banking/Financial Protection

- Enhanced Authentication
- FIDO-compliant hardware tokens being studied
- Requires physical proximity for transaction authentication
- Transaction Safeguards
- Cooling-off periods for high-risk transactions
- Enhanced fraud analytics
- Information sharing on money mule accounts
- Cryptocurrency Protection
- Working with MAS-licensed digital payment token providers
- Strengthening operational links with law enforcement

Public Education and Empowerment

- ScamShield Suite
- Launched September 2024
- Allows the public to check, report, and stay updated on scams
- ScamShield hotline (1799) for assistance
- Targeted Awareness Campaigns
- Monthly media campaigns
- Tailored to vulnerable population segments for specific scam types
Key Challenges and Trends
- Rising Financial Impact
- Total losses reached $1.1 billion in 2024 (a 70% increase from 2023)
- Evolving Tactics
- Scammers pivoting to local phone numbers
- Increased use of cryptocurrency to evade banking safeguards
- Exploitation of anonymity on messaging platforms
- Cross-Platform Nature
- Requires collaboration between government, tech companies, and financial institutions
- International dimension (implied by sophisticated criminal syndicates)

The Singapore approach appears multifaceted. It combines regulatory powers, technological solutions, industry collaboration, and public education to create a comprehensive anti-scam ecosystem. The emphasis on both preventive measures and empowering individuals to recognize scams suggests a balanced strategy to address this growing threat.
Maxthon

Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
Maxthon private browser for online privacyThis meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
The post Bank Customers Saved $73 Million Through Police-Bank Collaboration appeared first on Maxthon | Privacy Private Browser.