- E-commerce scams are the second-highest reported scam type in Singapore
- Cases more than doubled from 4,762 in 2022 to 9,783 in 2023
- The most common platforms for these scams: Facebook, Carousell, and Telegram
- Since January, at least 104 residents have lost at least $63,000 to e-commerce phishing scams
Clik here to view.

Recent Phishing Trend
- A new wave involves ads on social media (Instagram, Facebook, TikTok)
- Clicking these ads leads to phishing websites
- Victims are prompted to enter credit/debit card details and OTPs
- Unauthorized transactions occur, different from intended purchases
Clik here to view.

Safety Recommendations
The article shares best practices from the Ministry of Home Affairs:
- Verify seller profiles before purchasing
- Consider in-person transactions when possible
- Only transact with sellers whose identities are verified against government ID
- Use secure payment options like escrow services (used by Shopee and Lazada)
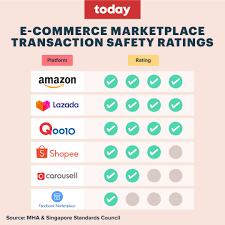
- Consult the E-commerce Marketplace Transaction Safety Ratings (TSR)
Clik here to view.
Success Story
The article includes a positive example of Mark Fernandez, who safely purchased a laptop on Carousell by:
- Check for the verified badge on the seller’s profile
- Reading reviews of past transactions
- Opting for cash on delivery
- Verifying the item’s condition before payment
Clik here to view.
E-commerce Scam Methods in Singapore
Based on the article, here’s an analysis of e-commerce scam methods prevalent in Singapore and their corresponding prevention strategies:
Common Scam Methods
- Platform-Based Scams:
- Facebook, Carousell, and Telegram are identified as the three platforms where e-commerce scams occur most frequently
- These likely involve fraudulent listings with non-existent or misrepresented products
- Social Media Advertisement Phishing:
- A recent trend highlighted in the article
- Attractive deals advertised on Instagram, Facebook, and TikTok
- Clicking these ads redirects users to phishing websites
- Victims are prompted to enter payment details and OTPs
- Unauthorized transactions occur that differ from the intended purchase
- Identity Misrepresentation:
- Implied in the article’s emphasis on verified sellers
- Scammers likely pose as legitimate sellers without proper verification
Clik here to view.

Prevention Methods
- Marketplace Safety Ratings:
- The Inter-Ministry Committee on Scams publishes E-commerce Marketplace Transaction Safety Ratings (TSR)
- Consumers are encouraged to consult these ratings before choosing platforms
- Seller Verification:
- Only transact with sellers whose identities have been verified against government-issued documentation (NRIC or UEN)
- Look for verification badges (like Carousell’s blue verified badge for users who complete all three verification methods)
- Check reviews of sellers’ past transactions
- Secure Payment Methods:
- Use escrow payment services (as offered by Shopee and Lazada)
- Money is released to sellers only after a specified period or when buyers confirm receipt
- Consider cash on delivery when possible
- In-person Transactions:
- Meeting sellers in person to verify goods before payment
- Check physical product condition before transferring funds
- Government Initiatives:
- Ministry of Home Affairs (MHA) publishes best practices
- Singapore Police Force’s Scam Public Education Office provides guidance
- The “Act against scams” series in partnership with the Singapore Police Force
Clik here to view.
Effectiveness Analysis
The case study of Mark Fernandez demonstrates how implementing multiple prevention strategies can lead to successful, scam-free transactions:
- He verified the seller’s credentials (blue badge)
- Reviewed past transaction feedback
- Used cash on delivery
- Physically inspected the product before payment
- Only transferred money after confirming product condition
This layered approach to security appears to be the most effective strategy against e-commerce scams, rather than relying on a single prevention method.
E-Commerce Scams
Clik here to view.

Trend Details
- 11,665 cases in 2024
- 19.23% increase from 2023
- Total losses: $17.5 million
- Average loss: $1,508 per case
Notable Example
A scammer named Foo Mei Qi:
- Defrauded 76 victims of $110,700 through fake Taylor Swift concert tickets
- Sold counterfeit tickets totalling $7,780
- Operated primarily on Carousell
Clik here to view.

Prevention Methods
- Never make payments before receiving items
- Be extra cautious on messaging platforms like Telegram
- Verify seller credentials thoroughly
- Be sceptical of deals for high-demand, sold-out items
- Use secure payment methods with buyer protection
- Meet sellers in safe, public locations for transactions
- Check the seller’s profile, reviews, and transaction history
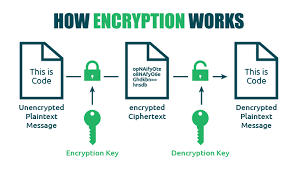
How Encryption Works
Clik here to view.

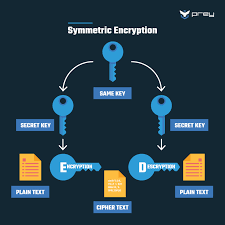
Encryption uses mathematical algorithms to convert plaintext (readable data) into ciphertext (scrambled data). Only those with the decryption key can convert the ciphertext back into usable information. There are two main types:
- Symmetric Encryption: Uses the same key for both encryption and decryption. It’s efficient but requires secure key exchange.
- Asymmetric Encryption uses a pair of keys—a public key for encryption and a private key for decryption—to allow secure communication without prior key exchange.
Clik here to view.
Key Encryption Applications for Privacy
Device Encryption
- Full-disk encryption: Protects all data on your computer or smartphone (BitLocker for Windows, FileVault for Mac, and built-in encryption for iOS and Android)
- File-level encryption: Protects individual files and folders
Clik here to view.

Communication Encryption
- HTTPS: Secures website connections (look for the padlock icon in your browser)
- End-to-end encryption: Used in messaging apps like Signal, WhatsApp, and others to ensure only you and your recipient can read messages
- Email encryption: Options include PGP (Pretty Good Privacy), S/MIME, or encrypted email services
Clik here to view.
Network Encryption
- VPNs: Create an encrypted tunnel for all your internet traffic
- Wi-Fi encryption: WPA3 is the current most substantial standard for wireless networks
Cloud Storage Encryption
- At-rest encryption: Protects stored data
- Zero-knowledge encryption: The provider has no access to your encryption keys
- Client-side encryption: Data is encrypted before leaving your device
Clik here to view.

Implementing Encryption in Your Digital Life
- Enable device encryption on all your computers and mobile devices
- Use encrypted messaging apps for sensitive communications
- Verify HTTPS connections when sharing personal or financial information
- Consider encrypted email for sensitive communications
- Choose cloud services with strong encryption policies
- Use a VPN when connecting to public Wi-Fi networks
- Password-protect and encrypt sensitive files and backups
Clik here to view.
Limitations to Consider
- Encryption can’t protect against malware already on your device
- Weak passwords can undermine even the strongest encryption
- Encryption doesn’t hide metadata (who you’re communicating with, when, how often)
- Some countries have laws limiting encryption use or requiring backdoors
Clik here to view.

Encryption is a fundamental aspect of digital privacy that works best as part of a comprehensive security strategy. By understanding and implementing appropriate encryption methods, you can significantly enhance your online privacy protection.
.
Identity Theft
Identity theft is a pervasive form of fraud that can have devastating consequences for victims. In this crime, the perpetrator steals an individual’s personal information to assume their identity. This stolen information can often be gathered from discarded documents such as bank statements, utility bills, or even phishing scams.
Once armed with this data, the criminal may choose to open accounts in the victim’s name, a process known as application fraud. They might apply for credit cards, loans, or utility services under pretences, leaving the unsuspecting victim to deal with the aftermath.
The emotional toll of identity theft can be immense. Victims often face financial losses and damage to their credit scores, which can take years. In today’s digital age, account takeovers have become a prevalent threat to unsuspecting victims. Criminals typically employ tactics such as phishing, vishing, or smishing to manipulate individuals into revealing their personal information.
Clik here to view.

Phishing often involves deceptive emails that appear to come from legitimate sources. These emails may prompt the victim to click on malicious links or provide sensitive details under the guise of verifying their identity.
Vishing, or voice phishing, involves phone calls in which scammers impersonate bank representatives or trusted entities to extract confidential information directly from the victim. Similarly, smishing involves text messages that lure individuals into divulging critical data.
Once armed with this personal information, the criminal can easily convince a bank to change the account holder’s address. This deception allows them full access to the victim’s financial accounts and resources.
Clik here to view.

Additionally, some criminals are skilled enough to bypass bank interaction altogether. They can use the obtained credentials to log into online accounts directly, executing unauthorised transactions without needing any further verification.
The consequences for victims can be devastating, leading not only to financial loss but also to emotional distress as they recover their stolen identities and secure their accounts. Consequently, individuals must remain vigilant and understand these risks to protect themselves against potential account takeovers for repair. Additionally, they may find themselves tangled in legal disputes as they try to prove their innocence.
Clik here to view.

Recovering from such a violation requires diligence and time, making it crucial for individuals to safeguard their personal information vigilantly. Implementing measures like shredding sensitive documents and monitoring credit reports can help prevent these types of crimes before they occur.
Maxthon
Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
Image may be NSFW.
Clik here to view. This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
The post E-Commerce Scams in Singapore appeared first on Maxthon | Privacy Private Browser.